Take control of privileged access to
your environment
The segura Privileged Access Management solution is built to keep your business and its most valuable assets secure. Prevent malicious account or credential access with segura.
Find Out How Our PAM (Privileged Access Management) Solution Can Help You:
Mitigate Risks and Maximize Productivity
Defend Against Attacks
Satisfy Audit & Compliance
Security at the Speed of Business
Empower Your Users
PAM CORE FLOW
How It Works
.png)
Cybersecurity Teams Love Segura
EASY TO USE
Our full-stack platform reduces complexity and requires 10x fewer resources for deployment than other leading solutions.Segura has received top scores for…
 Ease of Implementation
Ease of Implementation Ease of Administration
Ease of Administration Ease of Customization
Ease of Customization Usability and Intuitiveness
Usability and Intuitiveness(ITRG's Emotional Footprint for PAM Report 2023)
Enjoy peace of mind knowing that your organization is well-equipped to comply with regulatory requirements.
Segura PAM eases the stress of auditing and compliance with:




…and makes the process seamless and hassle-free
segura is the only PAM solution in the market that covers the complete privileged access management lifecycle.
Our solution provides governance before, during, and after privileged access events, keeping your organization safe from:




…and the resulting data loss, business interruption, fines, and other related issues.
Key Benefits
Our Privileged Access Management (PAM) solution not only ensures your organization's security but also provides unmatched business value.
![]()
Best Value
Thanks to our straightforward pricing, easy deployment and management, and low resource requirements, we offer up to 70% lower Total Cost of Ownership (TCO) than competing solutions.
![]()
Fastest Deployment
With our streamlined architecture, segura PAM can be deployed in hours or days as opposed to weeks or months (or even years).
Our fast deployment provides fast time to security and value.
![]()
Highest Customer Satisfaction
We value customer service first and foremost, and our users vouch for it.
We have the highest customer satisfaction rating and user recommendation rate in the industry on Gartner Peer Insights and segura is the only PAM vendor to have a full 5-star customer satisfaction rating.
![]()
Unparalleled User Experience
Let’s face it, if a security solution creates friction and slows users down, they’ll find a way to get around it.
segura PAM provides a top-tier user experience for both end users and admins, reducing friction and improving efficiency.
![]()
Highest Security
Our solution has been meticulously architected and developed to offer the highest possible security. segura PAM has been tested and certified time and time again to make sure your most valuable digital assets are in good hands.
![]()
Future-Proof Architecture
We have invested in modern architecture and development practices to give you a future-proof solution that scales and evolves with your needs and adapts in the ever-changing threat landscape.
![]()
No Hidden Costs
We offer a full-stack, plug-and-play platform with no hidden or additional costs. Our all-inclusive pricing means no surprise fees, just clear-cut benefits. Also, depending on your needs, you can select perpetual license or subscription pricing.
![]()
Easy upgrades, less downtime
segura’s stable, all-in-one platform offers built-in High Availability (HA) and Disaster Recovery (DR) capabilities, ensuring seamless upgrades and recovery from disasters with minimum downtime.
Segura is the PAM that Can
PAM used to be expensive, difficult, and complex. Not anymore with segura.
Up to 87% of security breaches are due to privileged credential misuse – accidental or otherwise.
Up to 56% of IT leaders have tried to deploy PAM systems but failed to reach their objectives due to complexity.
Up to 58% of CISOs would like to get a better PAM solution, but the solutions are too expensive.
Nearly 90% of IT teams would love to get a PAM that is easier to use.
SOPHISTICATED SECURITY OF ACCOUNTS WITH PRIVILEGES
How it works?
segura is the only PAM solution available on the market for complete Privileged Access Management that covers the entire privileged access lifecycle: identity management, privileged access management and auditing of all activities carried out in the privileged session. Our PAM method is used for continuous improvement of
privileged access lifecycle security.

Identity Management
The Scan Discovery feature is used to map and identify all assets connected to the environment and their respective credentials, including digital certificates. segura allows the mapping and integration of devices (including legacy applications), credentials, containers, playbooks, digital certificates and SSH keys. Gartner considered, in its Critical Capabilities and Magic Quadrant for PAM 2021 reports, segura's credential discovery capabilities as “best in class”.

Privileged Access Management
When configuring access groups, you can define the administrator users who will be allowed to be given a physical access password and the group of users who can use the remote access provided by the solution to access a target device or system. This allows segura to be recognized as one of the most granular solutions on the PAM market, which brings greater adherence to the organization's security policies.

Audit
All sessions on the system can be recorded in video and text, ensuring that any action on the system can be tracked for later audit, allowing you to quickly find the cause of a cyber incident or meet audit demands.
Key features
segura is the only PAM solution available on the market that covers the entire privileged access lifecycle.

Secure Vault and Password Manager
Takes highly privileged administrative accounts and passwords out of the direct control of users and stores them securely in a software vault that regularly rotates passwords based on your policies.

SSH Key Management
Manages trust relationships between SSH keys and systems. Controls and traces SSH key use.

Enhanced Auditing, Reporting, and Compliance
Records every session within the system, ensuring comprehensive tracking of all actions. This robust auditing capability allows users to quickly find the cause of any cyber incident and meet compliance demands.

Behavioral Analysis
Identifies and responds to any change in behavior patterns and user access profiles.

Session Monitoring, Recording, and Control
Monitors user activities and detects suspicious events in real-time, including the possibility of pausing or ending the user’s session simply and quickly. Records sessions for forensics and auditing. We offer better performance delivering up to 7 times more video storage capacity than competing solutions.
.png)
Automation
Automates routine workflows to decrease the workload of your IT and security staff and reduce user friction.
![]()
Approval Workflows
Implements multilevel approval flows and validation provided by the requesting user on remote sessions or password-viewing cases, with alerts via email or SMS.
Service Account Governance
Secures and controls your service accounts, removing passwords from the hands of your users and automatically changing service account passwords on a regular basis.
![]()
Multi-Factor Authentication
Validates privileged users with secure Multi-Factor Authentication and secures access to business resources with Single Sign-On.
Granular Access Control
Provides and revokes privileges for local user access on Windows, Linux, Unix, Databases, and Active Directory platforms without the need to install anything on the target device.
![]()
Visual Dashboards
Updates the interactive dashboards with real-time insights into the security configurations and privileged access activities across your infrastructure. The dashboards can also be used to identify and mitigate any risky behavior instantly.
![]()
Account and Discovery
Seamlessly maps and identifies all of the environment’s connected assets, including their credentials and digital certificates. This offers comprehensive integration for devices, legacy applications, credentials, containers, playbooks, and SSH keys.
![]()
Scripting and Integrations
Integrated and fully supported macro tools for multiple protocols (SSH, RDP...) and APIs. Seamless compatibility across operating systems, web applications, network and security devices, virtualization environments, databases, directory systems, remote access and monitoring tools, as well as mobile devices and browsers.
![]()
Database Proxy
Streamlines your database management with integrated PAM features to guarantee secure operation. Administrators have the power to enable, monitor, and restrict operations. Users can use their preferred client to access databases directly from their workstations without the need for passwords. This cutting-edge feature also includes a pioneering command filter for Oracle.
Who is it recommended for?
The solution is recommended for companies in the following scenarios:
- Companies with more than 10 users.
- Companies that received points of attention in auditing.
- Companies that need to reduce operating costs.
- Companies that must comply with cybersecurity rules and regulations.
- Companies that want to implement the best security practices.
- Companies that have suffered a security incident.
Deploy the Way You Like It
Every customer environment is different, so you have the freedom to deploy our PAM solution in the way that best suits your needs, whether it’s through a SaaS, private cloud, hybrid cloud, or on-premises solution. Regardless of how you deploy, you get the same great features, usability, and value.
We host your solution and provide it as a seamless service with automated upgrades and patches for reduced total cost of ownership.
Deploy and manage your segura instance in your private cloud environment or use a hybrid approach.
Deploy in your data center to meet regulatory compliance or organizational needs.When your needs change, you can easily migrate to cloud or SaaS with our full support.
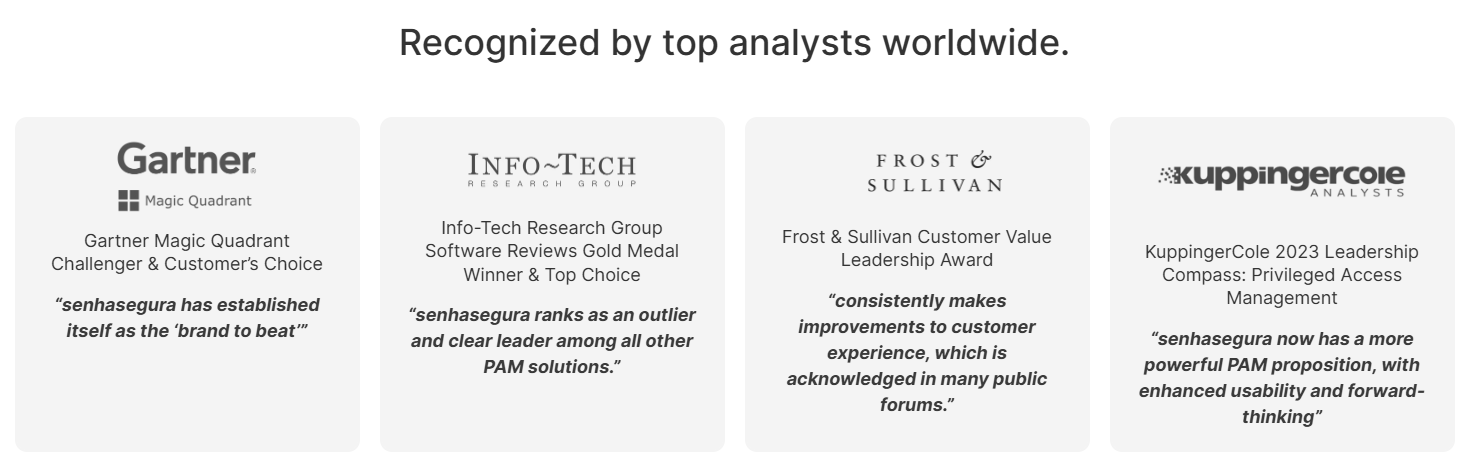

Leading PAM for Cybersecurity Resilience towards a Prosperous Future.
Consistently recognized as Leaders by IT Consulting Firms and clients, growing every year. We strive to ensure the sovereignty of companies over privileged information.

For Datasheet Please Click here: